
Asset Protection Strategies for PE Deal Teams
Cyber & information security services
Executive summary
At Diligize we offer a range of Cyber and Information security related service offerings tailored to add value to Private Equity and their portfolio companies, principally through asset protection.
These services are driven by our deep understanding of the needs of the Private Equity industry in relation to all facets of Cyber and Information security and directly result in service offerings in the following key areas. On average, Diligize provides these services about 60% cheaper than other suppliers:
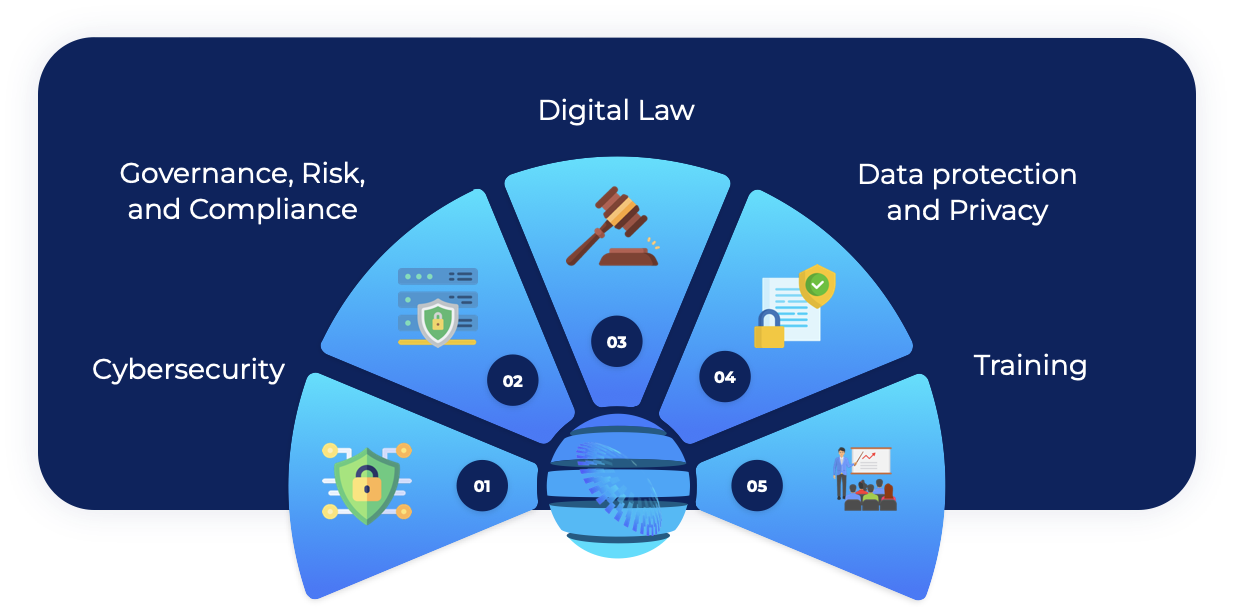
Cyber maturity assessment
A 360-degree review of current cyber and information security practices at an organisation.
Full Cybersecurity-as-a-Service
To manage all cyber security concerns and provide specialist services such as legal consultation, penetration testing, incident management, and cybersecurity training on an as-needed basis.
Certification assistance
Aid in attaining Cybersecurity certifications and accreditations
Expertise
Confidential general cyber and information security consultancy and assessments.
There are many key considerations for maintaining robust cyber and information security concerns at PE funds. These can be effectively managed by applying best-practice Cyber and Information governance in place and strategies such as outsourcing these concerns to cost-effective service providers who ensure 24x7 coverage and management. Such an approach is advisable as cyber and information security is a complex discipline where a high level of expertise is required to be able to effectively respond to the ever-changing security landscape.
To progress to best-practice cyber and information security Diligize offers the following services:
Private equity perspectives
Importance and considerations
Cyber and information security is critically important to private equity (PE) funds for many reasons. PE funds deal with sensitive financial information, proprietary data, and investment strategies, making them attractive targets for cyberattacks and data breaches. below are some key considerations for maintaining robust cyber and information security concerns at PE funds:
- Protecting Confidential Information: PE funds handle sensitive financial data, business strategies, and investment portfolios. Effective cybersecurity safeguards this information from unauthorized access, theft, or disclosure, preserving the confidentiality of their investments and strategies.
- Reputation Management: A data breach or cyberattack can lead to a loss of trust among investors and stakeholders. Maintaining a strong cybersecurity posture helps protect fund reputation, demonstrating rigour in safeguarding sensitive information.
- Compliance with Regulations: Many jurisdictions have stringent data protection and cybersecurity regulations. Compliance with these regulations, such as GDPR, HIPAA, or specific financial industry requirements, is essential to avoid legal consequences and financial penalties.
- Investor Confidence: Institutional and individual investors in PE funds want assurance that their investments are secure. Robust cybersecurity measures can attract and retain investors by instilling confidence in the fund’s ability to protect their capital and sensitive data.
- Protecting Deal Flow: Maintaining the confidentiality of potential investment opportunities and deal-related information is crucial. Effective cybersecurity measures prevent leaks or breaches that could compromise the fund’s competitive advantage.
- Reducing Financial Risk: Cyberattacks and data breaches can result in significant financial losses. Cyber insurance, while not a substitute for strong security measures, can help mitigate financial risks associated with cyber incidents.
- Business Continuity: Cyberattacks can disrupt operations and lead to downtime. Investing in business continuity and disaster recovery planning ensures that the fund can continue to operate even in the face of a cyber incident.
- Intellectual Property Protection: PE funds may hold proprietary investment strategies and models. Ensuring the security of these intellectual assets is crucial to maintaining a competitive edge in the market.
- Competitive Advantage: Demonstrating a commitment to cybersecurity can set a PE fund apart from its competitors. It can be a selling point when attracting investors and engaging with portfolio companies.
- Insider Threat Mitigation: Internal actors, such as employees or partners, can pose a significant security risk. Implementing controls and monitoring systems can help detect and mitigate insider threats.
- Cyber Due Diligence for Investments:. Conducting cyber due diligence is advisable when considering investments in technology companies or those with significant digital assets. Conducting cyber due diligence helps assess the target’s cybersecurity posture and any potential liabilities.
Each of these considerations may be addressed through the measures indicated. However, these measures often need ongoing review and monitoring to remain effective. Diligize, and their outsourced Cyber Security as a Service offering, can ensure that appropriate measures remain in place and evolve as operating conditions change.
Cyber & information security services
Cyber and information security is critical for PE funds to protect their investments, maintain investor confidence, comply with regulations, and preserve their reputation.
Investing in cybersecurity is an essential aspect of risk management and operational excellence in the private equity industry.
Cyber Security
Technical cybersecurity services
Cybersecurity
DAY TO DAY / PERIODIC ACTIVITIES PERFORMED
Cybersecurity is underpinned by a range of day-to-day and periodic practices that are performed to monitor the business landscape for weaknesses or changes that could permit a breach of security. Diligize provides a full range of services to support all these activities. The activities supported include the following.
01.
Security audits
- Penetration testing
- Web Service Pentesting
- Pentesting App
- Pentesting of Networks
- Pentesting in virtualized environments
Red team
02.
- Red Team consists of simulating a cyberattack aimed at an organisation, which must be verified knowing only the name of the organisation or defining an initial starting point, the possibility of having access to the systems, compromising them, and the impact this could have on the business.
Intrusion test
03.
- Wi-Fi Audit
- Audit code-development cycle
- Auditing apps and webservices
- Security review, hardening and bastioning
Cloud Environments audits
04.
- To provide knowledge about the security situation in the services of a contracted Cloud provider, and its assurance regarding the importance of the business processes they support.
Cyber and threat awareness
Managing threats and creating a cyber security mindset
Effective cyber and information security requires an awareness of threats and the creation of an organization-wide mindset where every member of the organization understands their roles and responsibilities in terms of security.
Training alone is not sufficient, day to day activities and ways-of-working must incorporate this security mindset and maintain vigilance as conditions change.
Social Engineering
Diligize carries out the following simulations, so that you can know the real behavior of your employees in the face of cyberattacks under different attack vectors such as Phishing, Ransomware, etc.

Social Engineering
Diligize carries out the following simulations, so that you can know the real behavior of your employees in the face of cyberattacks under different attack vectors such as Phishing, Ransomware, etc.
Live Hacking
Live hacking workshops aimed at employees and senior management, which help uncover how attacks are generated. Some of the topics offered include: phishing simulation, simulation of ransomware infection, malicious hardware devices, etc.

Live Hacking
Live hacking workshops aimed at employees and senior management, which help uncover how attacks are generated. Some of the topics offered include : phishing simulation, simulation of ransomware infection, malicious hardware devices, etc.

Cyber Awareness
We offer specialist and awareness-raising courses on cybersecurity, to create a culture of awareness among employees, making them an effective first line of defence: through E-learning, face-to-face/online specific courses, sessions, and workshops.

Cyber Awareness
We offer specialist and awareness-raising courses on cybersecurity, to create a culture of awareness among employees, making them an effective first line of defence: through E-learning, face-to-face/online specific courses, sessions, and workshops.
Governance, risk, & compliance
Taking control and managing cyber and information security
Governance, risk, & compliance
An effective management model for cyber and information security integrates the functions of Corporate Governance, Risk Management and Regulatory Compliance
- Security Governance
- Supplier security
- Audits and controls review
- Security Standard accreditation
- Cloud Compliance Audits
- Critical Infrastructure Protection
- Incident Response Plan
- Security Master Plans
- Technical Security Offices
- CISO AS A SERVICE
Diligize addresses all Applicable standards and governance: Such as ISO 27001, Cyber Essentials, NIST(US), ENISA(EU) and others.

Chief information security officer (CISO)
A CISO is often an essential role. CISO can be in-house or can be provided by an external supplier such as Diligize as a virtual CISO (monitoring) or CISO-as-a-Service (providing 24x7 management.)

VIRTUAL CISO

CISO AS SERVICE
FULL-TIME CISO
Security master plans
Definition and prioritisation of a set of information security projects, with initial assessment.

Strategy definition
1
Risk analysis
2

Risk management plan
3

Plan submission and approval
4
Implementation
5
Digital law
Law and technology, legal perspectives
We design and implement sustainable digital law solutions to meet your needs and provide legal certainty in your activities to assist growth opportunities for your business.
Digital law, often referred to as cyber law or internet law, is a branch of legal studies that encompasses the rules, regulations, and legal issues related to the use of digital technology, the internet, and information and communication technologies (ICTs). It focuses on the legal aspects of various digital activities, including online communication, e-commerce, cybersecurity, intellectual property rights, and data privacy. Digital law seeks to establish a framework for governing and regulating these activities in the digital realm.
Key aspects and topics within digital law include:
- Cybersecurity: Digital law addresses issues related to the protection of computer systems, networks, and data from cyber threats such as hacking, malware, and data breaches. It often involves regulations and legal requirements for organizations to safeguard their digital assets.
- Intellectual Property: This area of digital law deals with copyright, trademark, patent, and trade secret laws as they apply to digital content, software, and online intellectual property rights. It aims to protect creators and innovators from unauthorized use or infringement.
- E-commerce: Digital law regulates online transactions, electronic contracts, and consumer rights in the context of buying and selling goods and services over the internet. It covers issues like online payment methods, consumer protection, and dispute resolution.
- Data Privacy: This aspect of digital law focuses on protecting individuals’ personal data and privacy rights in the digital space. Laws such as the General Data Protection Regulation (GDPR) in Europe and various data privacy regulations in other regions set guidelines for the collection, processing, and storage of personal information.
- Online Speech and Freedom of Expression: Digital law addresses issues related to freedom of speech, hate speech, defamation, and online harassment in the context of social media, websites, and other online platforms.
- Jurisdiction and Cross-Border Legal Issues: The internet transcends geographical boundaries, which can lead to complex jurisdictional issues. Digital law seeks to clarify which legal jurisdiction applies in various online cases and how international conflicts are resolved.
- Digital Crimes: It encompasses legal aspects related to digital crimes such as cyberbullying, identity theft, online fraud, and cyberterrorism. Law enforcement and legal authorities work to investigate and prosecute these offenses.
- Regulation of Internet Service Providers (ISPs): Digital law often includes regulations governing the behaviour and responsibilities of internet service providers, including issues related to net neutrality and content filtering.
- Social Media and Online Platforms: The legal framework surrounding social media platforms and other online services includes issues such as content moderation, liability for user-generated content, and terms of service agreements.
Digital law is a dynamic field that evolves alongside technology, playing a crucial role in ensuring that the digital world remains a safe and fair environment for individuals, businesses, and organizations. Diligize specializes in digital law to help navigate these complex issues and provide guidance on compliance and legal rights in the digital realm.
Data protection & privacy
Services provided and related topics managed
Diligize addresses the privacy and data protection topics indicated as well as providing the DPO focused services indicated.
GDPR

DPO as a service

Consulting, monitoring and maintenance

Whistleblower channel

Analysis and study of international regulations

ISO/IEC 27701 – Security techniques certification

EIPD/PIA (Privacy Impact Assessment)

International Data transfers

Security breach support

RISK4ALL Privacy and Security Management Software

Training
Vigilance, awareness and involvement
Diligize follows an approach in which the analysis and detection of needs is carried out recurrently at different stages of the training process.
Our methodology, as well as contemplating the entire training process, allows continuous improvement to be a fundamental part of achieving success.

Global Provider of Training and Awareness in Cybersecurity, Privacy and Governance.

100% flexible, adapted to the needs of the client.

In-house production with pedagogical criteria and practical application.

Training offerings developed under SCORM, ensuring compatibility with all open-source platforms.

Adaptability to awareness platforms: Campus, Proofpoint, Knowbe4, Kymatio, etc.

Vigilance
Resources

Standard awareness resources
1
Catalogue of over 50 themes of e-learning resources that follow different pedagogical methodologies.
Social engineering simulations
2
We perform simulations with different attack vectors to test the alert status of your employees.

Specialists courses
3
We have specialised courses in the different subjects to train professionals, approved by certification agencies.

ADHOC awareness courses
4
We produce customised training resources based on any related thematic content or internal policies and procedures.
Strategic awareness plans
5
We support clients during the process of defining, designing, implementing and measuring awareness plans.

Awareness platforms
6
With our own eCampus, we use different platforms to support the execution of training activities.
